16 min to read
Data privacy has become a pressing concern in today's digital age, as individuals and organizations generate and exchange vast amounts of data on a daily basis. This has resulted in strict policies and guidelines for individuals and companies to follow, to ensure that data is handled appropriately.

This article will discuss key reasons why data privacy should be taken seriously, emphasizing the crucial role it plays in different aspects for businesses as well as exploring ways for maintaining data privacy.
Safeguarding Personal Information
Data privacy is vital for safeguarding personal information in the digital realm. Today, personal data such as names, addresses, social security numbers, financial details, and health records are stored and transmitted across various platforms, making them vulnerable to identity theft, hacking, and illegal surveillance. By taking data privacy seriously, individuals can protect their sensitive information from falling into the wrong hands, thus reducing the risk of identity fraud and other malicious activities.
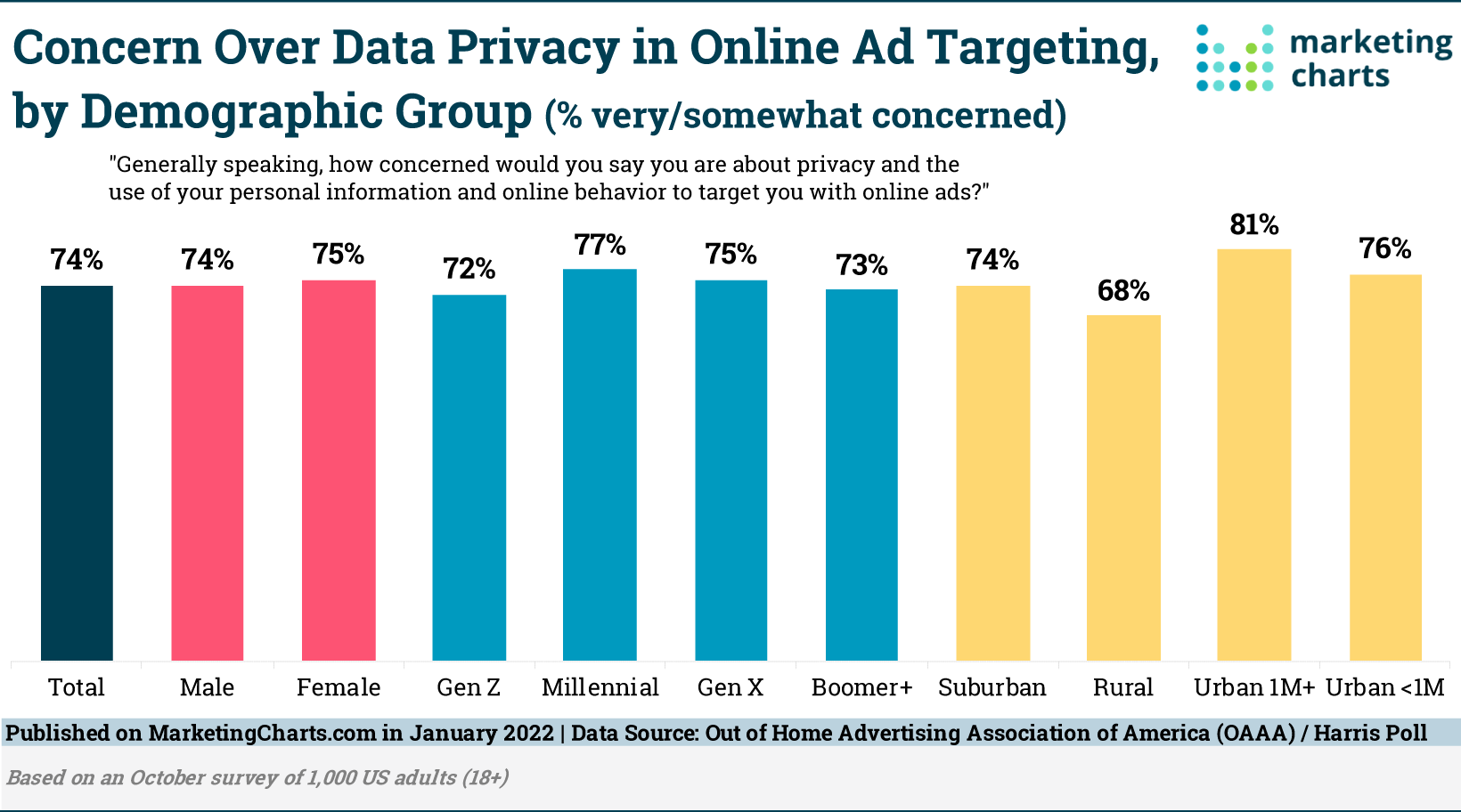
Key Insights: Overall Concern is High: The chart shows that there's a significant level of concern across all demographic categories, with the overall average at 74%.
By Gender:
- Male (74%) and Female (75%) respondents have almost identical levels of concern about online data privacy. The minimal difference indicates that concern over data privacy transcends gender lines.
Generational Differences:
- Gen Z (72%) and Millennials (77%) exhibit a higher level of concern compared to Boomers+ (73%), but the concern levels are still quite close. Surprisingly, it's Gen X (75%) that matches the overall average.
One might expect younger generations, being digital natives, to be less concerned due to their familiarity with technology. However, their high concern could also indicate a greater awareness of data privacy issues.
By Living Area:
- Respondents from Urban areas with a population of more than 1 million (81%) show the highest level of concern among all categories.
- This is followed by those from Urban areas with a population of less than 1 million (76%), Suburban areas (74%), and lastly, Rural areas (68%).
It's plausible that individuals in more densely populated areas are exposed to more digital advertising and might have a heightened awareness of data-tracking practices. Alternatively, urban residents might simply have more online interactions and digital transactions, leading to increased privacy concerns.
Why the Differences?
- Generational Differences: Digital natives (Gen Z and Millennials) have grown up with technology and are likely more aware of the kind of data being collected. Gen X and Boomers, on the other hand, might be more cautious because of their broader life experiences and historical context.
- Urban vs. Rural: The difference in concern between urban and rural respondents could be attributed to the different levels of online exposure and technological infrastructure. Urban areas often have better internet access, and residents might have more interactions online, leading to heightened awareness and concern about data privacy.
There is a worry, about the privacy of data among groups of people. However the reasons behind these concerns can be complex. Influenced by factors like activities, familiarity, with technology and knowledge of data gathering methods.
Maintaining Trust and how it evolved
Ensuring the privacy of data is of importance, in todays interconnected world. People need to feel assured that the entities collecting their data will handle it responsibly with respect and security. When organizations prioritize data privacy they can build transparent relationships, with their customers, clients and partners. This fosters trust, loyalty and long term engagement.Promoting Innovation
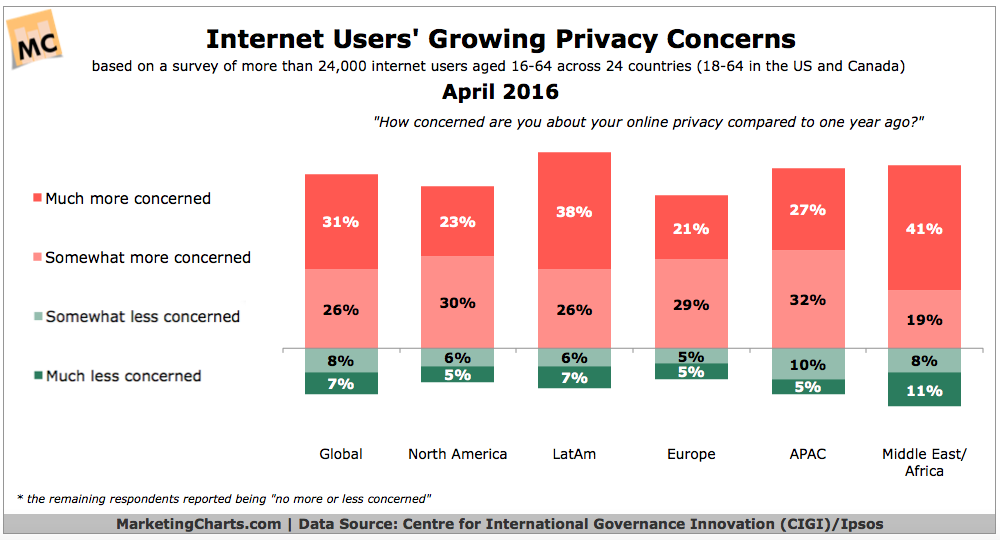
Globally, 57% were either "much more concerned" or "somewhat more concerned" about their online privacy compared to the previous year. This indicates a growing awareness and concern regarding online privacy issues among internet users worldwide.
Regional Differences:
- North America: 54% of respondents were more concerned about their online privacy than the year before, which is slightly below the global average.
- LatAm: 61% of users in Latin America expressed increased concern, which is above the global average.
- Europe: 49% of European users felt an increased concern, below the global average.
- APAC: A significant 68% of users in the Asia-Pacific region expressed more concern, making it the region with the highest increase in privacy concerns.
- Middle East/Africa: 60% of respondents were more concerned about their online privacy.
Timeframe: The presented chart is from 2016, which is significantly older than the first chart from January 2022. This older chart serves as a historical perspective, showing that concerns about online privacy have been escalating for several years.
The first chart looked at current levels of concern about data privacy in online ad targeting. In contrast, this chart focuses on the change in levels of concern compared to a year prior. Therefore, this chart underscores the dynamic nature of these concerns, suggesting that awareness and unease are growing year over year.
While the first chart highlighted urban-rural and generational divides, this chart emphasizes geographical distinctions. It's worth noting the heightened concerns in regions like APAC and LatAm compared to North America and Europe. These differences can stem from varied factors like data breaches, evolving internet usage patterns, regulatory changes, or growing awareness of surveillance technologies in these regions.
Both charts collectively indicate that data privacy concerns have not only remained consistent but have also seen significant growth over time, with variances across demographics and regions. The concerns surrounding online privacy seem to be universal, albeit with nuances in intensity and reasons across different groups and geographical areas.
Mitigating Financial Losses
Protecting data privacy is extremely important to prevent losses that can occur due, to data breaches, cyber attacks and unauthorized access. The consequences of a data breach are not limited to damages; they also include legal actions, penalties imposed by regulatory authorities harm to reputation and erosion of customer trust. To minimize the likelihood of incidents and maintain business operations organizations need to prioritize data privacy and establish robust measures, for secure data protection.
It's a global problem. This next chart presents the "Cost of a data breach by country or region" and measures the costs in US$ millions. It highlights the financial implications associated with data breaches in various countries and regions.
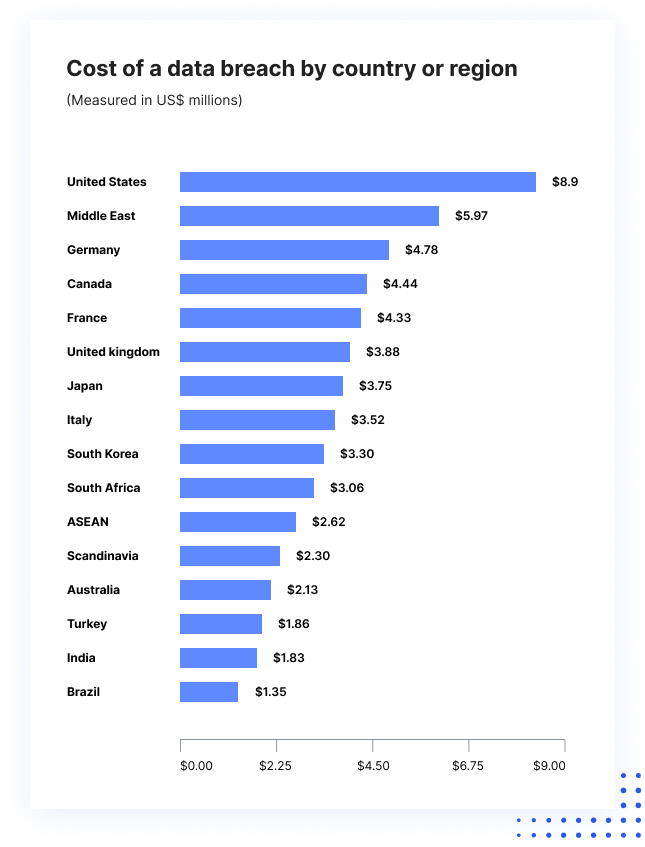
- United States Leads in Costs: The United States stands out with the highest data breach cost, which is $8.9 million. This could be attributed to the presence of numerous large corporations and stringent regulatory penalties, among other factors.
- Middle East and European Countries: Following the U.S., the Middle East has the second-highest cost at $5.97 million. European countries like Germany, France, and the United Kingdom also have higher breach costs, ranging from $3.88 million to $4.78 million. The European Union's General Data Protection Regulation (GDPR) could play a role in these figures, as non-compliance can result in hefty fines.
- Asia-Pacific Region: Japan and South Korea have costs of $3.75 million and $3.30 million, respectively. These figures could reflect the technological advancement and high digital adoption rates in these nations
- Emerging Markets: Countries like India and Brazil showcase lower data breach costs, with $1.83 million and $1.35 million, respectively. While these costs are lower relative to other countries on the list, the implications for local businesses can still be substantial.
- Regions as a Whole: The chart also includes regional aggregates such as ASEAN (Association of Southeast Asian Nations) and Scandinavia. Scandinavia's costs stand at $2.30 million, slightly less than the ASEAN region at $2.62 million. Regional figures like these can offer a broader perspective on areas with shared economic or regulatory environments.
Preserving Individual Rights
Ensuring data privacy plays a role, in safeguarding rights such as privacy, freedom of speech and protection against discrimination. It is vital that personal information remains confidential and individuals maintain authority, over the gathering, utilization and dissemination of their data. By placing importance on data privacy societies can steer clear of the downsides linked to surveillance, manipulation and discrimination stemming from information.
We don't have data after 2022. but based on that there are several things we can highlight.
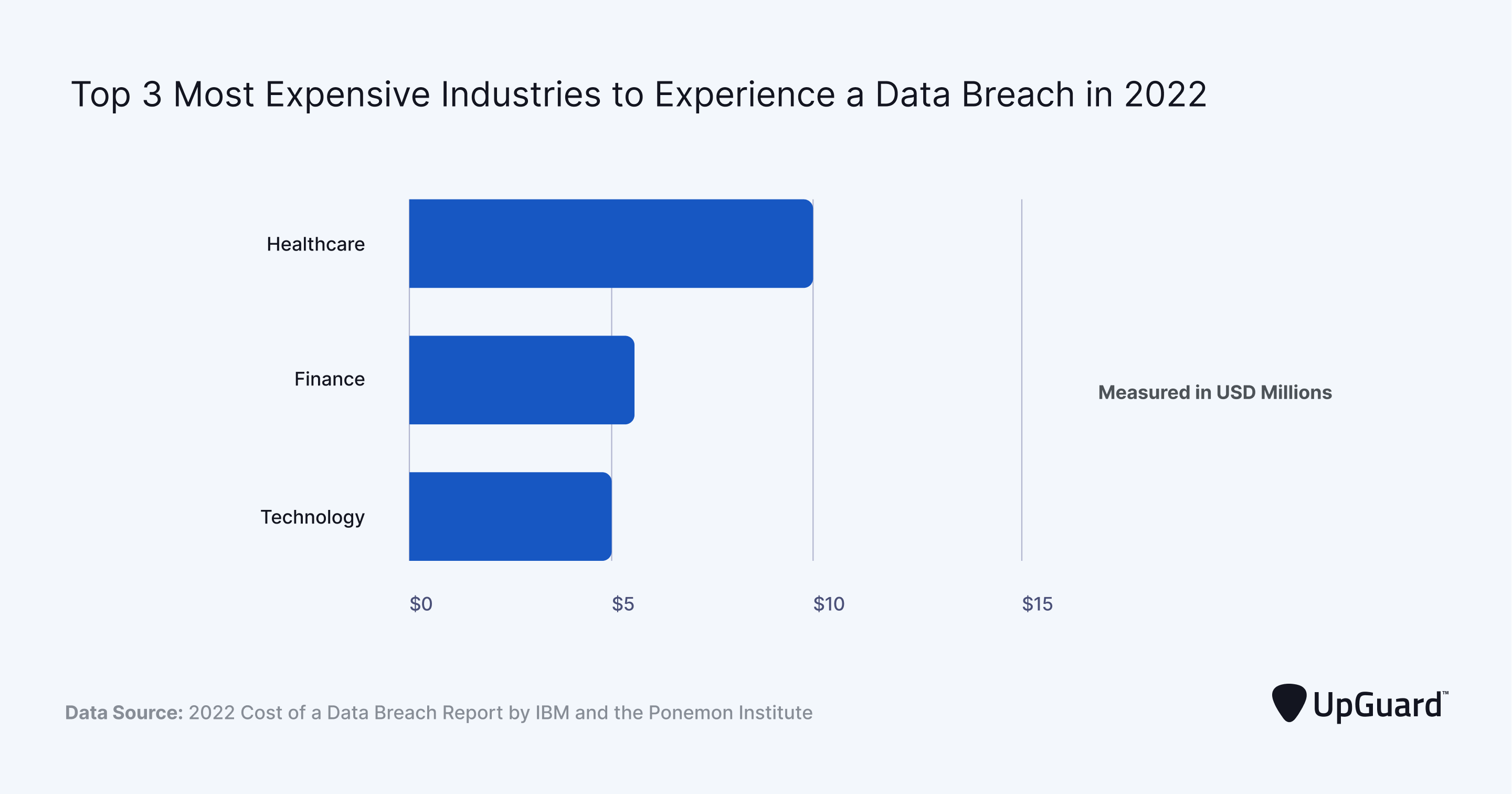
- Healthcare stands out as the industry with the highest cost associated with data breaches, indicating the significant importance of patient data and the stringent regulations surrounding it.
- Finance follows closely, emphasizing the critical nature of financial data and the trust that institutions must maintain with their clients.
- Technology is also notably affected, which underscores the valuable nature of technological data and the vast amounts of personal and proprietary data tech companies often handle.
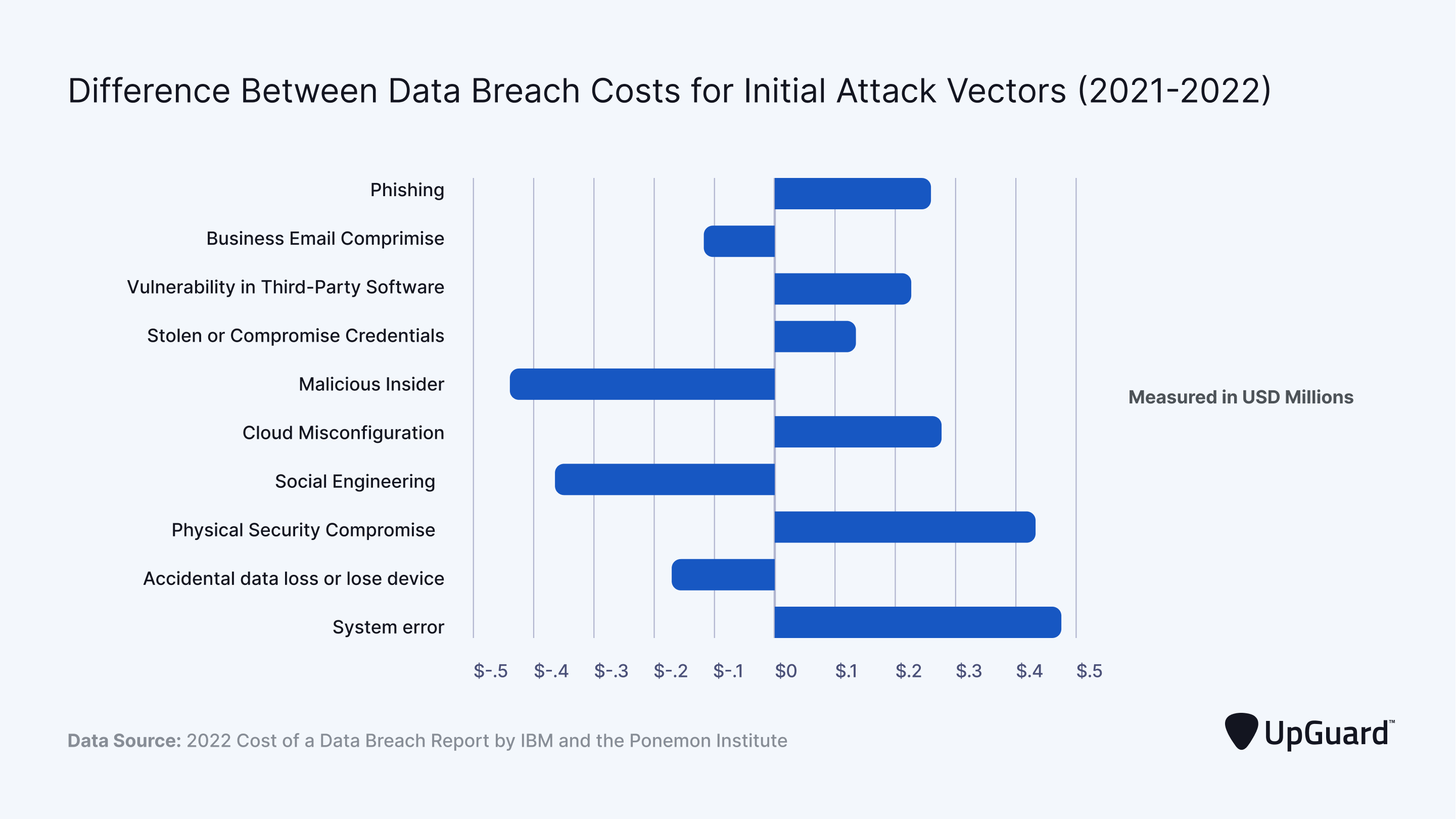
Difference Between Data Breach Costs for Initial Attack Vectors (2021-2022):
- The most expensive vectors, such as Phishing and Business Email Compromise, involve direct interaction with individuals, highlighting the vulnerability of human error in the security chain.
- Vulnerabilities in Third-Party Software and Stolen or Compromised Credentials represent other major cost contributors. These vectors illustrate the risks associated with relying on third-party solutions and the importance of strong credential management.
- Factors like Malicious Insiders and Cloud Misconfiguration further emphasize the need for robust internal security protocols and thorough oversight of cloud configurations.
- Interestingly, direct physical methods like Physical Security Compromise have lower associated costs compared to digital vectors, but they still represent a considerable risk.
The data emphasizes the growing need for comprehensive cybersecurity strategies across all industries and the importance of continuous employee training to mitigate risks. Furthermore, it showcases the potential financial implications that organizations might face if they don't prioritize data security.
Ways To Maintain Data Privacy
Implementing robust data protection Policies and Practices
It is important for businesses to create defined rules and procedures that govern the gathering, storage and handling of data. These guidelines should clearly outline the responsibilities of employees restrict access, to information to authorized personnel only and enforce the use of passwords and encryption methods. Conducting security audits and assessments is also beneficial in identifying any vulnerabilities and ensuring compliance, with data protection regulations.
Frequent Auditing
Businesses can enhance data privacy by regularly monitoring and auditing their systems for any vulnerabilities or potential threats. Deploying data privacy software, intrusion detection systems, and employing ethical hackers for penetration testing can help identify weaknesses in the system. Monitoring network activity and data access logs can enable a proactive response to potential breaches. Regular audits of data processing activities and risk assessments can also assist in identifying areas for improvement and ensuring ongoing compliance with data protection measures.
Educate Employees About Data Privacy
It is important for employees to understand the dangers that may arise from mishandling data. This includes being vulnerable, to phishing attacks or unintentionally disclosing information. Regular training sessions can provide employees with insights on how to follow practices, such, as identifying suspicious emails maintaining strong passwords and securely sharing files. By prioritizing data security and promoting a culture of vigilance businesses can reduce the risk of data breaches resulting from mistakes.
Adopt Secure Data Storage Practices
Storing data on secure servers with strong access controls, firewalls, and intrusion detection systems can help defend against external threats. Regular backups, stored in encrypted and off-site locations, can mitigate the impact of potential data loss caused by system failures or ransomware attacks. Additionally, businesses should regularly evaluate their service providers and ensure they adhere to stringent data security standards.

There are arguments, for giving due importance to data privacy as evident from the details provided on this page. As the digital world keeps advancing it becomes increasingly crucial to tackle the issues arising from data privacy. It is by working together to safeguard personal information that we can guarantee a secure, trustworthy and morally upright digital space, for both individuals and organizations.
Best Practices for Implementing a GDPR Project
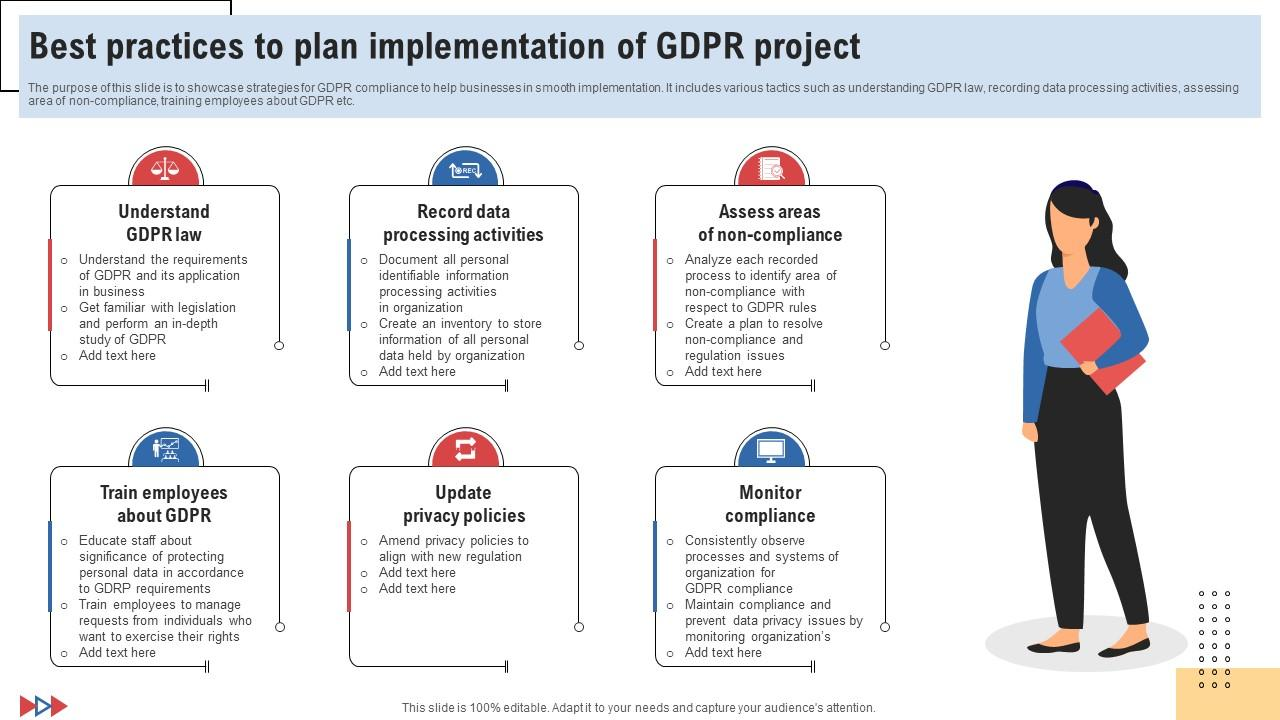
Understand the GDPR Law:
- Familiarize yourself with the specific requirements of the GDPR and how they apply to your business operations.
- Dive deep into the legislation to gain a comprehensive understanding of the GDPR. This could involve attending seminars, workshops, or engaging with legal experts specializing in GDPR.
Record Data Processing Activities:
- Maintain thorough documentation of all personal identifiable information processing activities undertaken by the organization.
- Establish a robust inventory system that categorizes and stores all personal data systematically held by your organization.
Assess Areas of Non-Compliance
- Regularly review and analyze your data processing activities to identify any areas where you might not be in full compliance with GDPR rules.
- Develop a proactive plan to address and resolve any identified issues related to non-compliance and regulatory concerns.
Train Employees about GDPR:
- Educate your staff about the importance of data protection and the nuances of GDPR. This could involve training programs, workshops, and regular updates.
- Equip your employees with the skills and knowledge to manage requests from individuals who wish to exercise their rights under GDPR.
Update Privacy Policies:
- Revisit and revise your organization's privacy policies to ensure they are in line with GDPR requirements.
- Make the necessary amendments to your policies and ensure that they are easily accessible and understandable for your users or clients.
Monitor Compliance:
- Establish a system to consistently oversee the data processing systems and activities in your organization, ensuring they adhere to GDPR standards.
- Put mechanisms in place to maintain compliance and address potential data privacy issues. This could involve regular audits, feedback systems, and real-time monitoring.
The simple example of customer ‘John Doe’ who holds several active bank accounts and is asking for erasure of his personal data, illustrates this challenge:
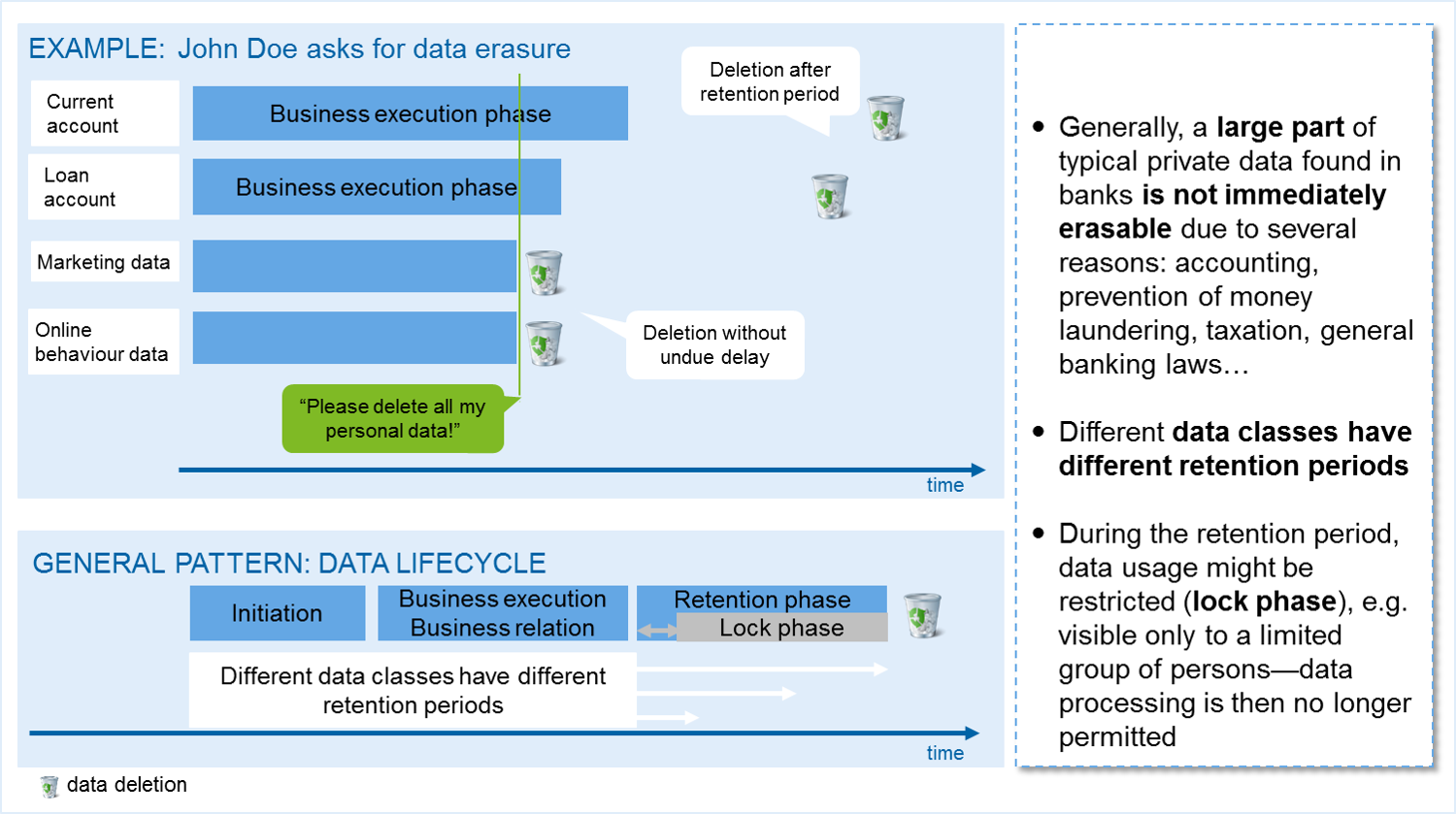
When a client requests the deletion of all his personal data:
- Current Account & Loan Account Data: Even though he makes this request during the business execution phase, the data is not immediately deleted. It undergoes a retention period before eventual deletion. This is likely due to various regulations and requirements related to banking.
- Marketing Data: This data is promptly deleted after his request.
- Online Behavior Data: This data also gets deleted without any undue delay after his request.
Some data types can be promptly deleted; others have mandatory retention periods. This is mainly because banks hold a lot of sensitive data that are bound by several laws and regulations, such as those related to accounting, money laundering prevention, taxation, and general banking.
General Data Lifecycle Pattern
The data lifecycle is broadly divided into three phases:
- Initiation: When the data is first acquired or generated.
- Business Execution/Business Relation: The period when the data is actively used for various business purposes.
- Retention Phase: After active use, data isn't immediately deleted. It enters a retention phase where it's stored for a certain period for regulatory or business reasons.
- Lock Phase: During the retention period, there might be a phase where the data usage is highly restricted, making it accessible only to a specific group of individuals. During this phase, further data processing is generally not allowed.
The "data deletion" symbol signifies the end of the data lifecycle, where the data is finally erased from the system.
Some Takeaways
- Not all data can be immediately deleted upon request, especially in the banking sector. Various regulations ensure data integrity and security.
- Different types of data have distinct retention periods, after which they can be safely deleted.
- There's a 'lock phase' during the data's lifecycle where its processing is restricted to uphold data security and privacy.
What are the biggest differences between GDPR and CCPA

Here is the word for our American Clients:
CCPA vs. GDPR:
CCPA
Companies that serve Californian residents and have at least $25 million in annual revenue, possess the personal data of 50,000+ people, or earn more than half of their annual revenue selling Californian residents' personal data.
Personal information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked with a particular consumer or household.
Penalties for intentional violations can reach up to $7,500 per violation and $2,500 for unintentional violations.
GDPR
Any organization that processes the personal data of EU citizens, regardless of the organization's location.
Personal data relating to an identified or identifiable natural person.
Fines can reach up to €20 million or 4% of the firm's global annual revenue from the preceding fiscal year, whichever amount is higher.
The CCPA and GDPR serve a purpose of safeguarding individuals privacy. They have distinct scopes and requirements. Companies that operate in both California and the European Union must ensure compliance, with both sets of regulations.
It's worth noting that the penalties for non compliance under GDPR are notably more severe than those under the CCPA highlighting the EUs stance on data protection. Both regulations emphasize transparency. Giving consumers control over their data.
Regardless of their size or location organizations must take an approach in understanding and adhering to these regulations if they handle data from these regions.
Staying up to date on regulations is crucial for businesses as global data privacy laws continue to evolve. Seeking guidance, from data privacy experts is advised to ensure compliance.

How Codedesign Can Assist Clients with GDPR Compliance:
- GDPR Audit & Gap Analysis: Codedesign can thoroughly audit your digital properties to identify areas where you may not be GDPR compliant. This includes reviewing data collection methods, storage practices, and data processing activities.
- Consent Management: We ensure that your websites, apps, and digital platforms have proper consent mechanisms in place, allowing users to explicitly opt-in or out of data collection, in line with GDPR requirements.
- Data Mapping & Management: Our team can help you track and map out where your data comes from, how it's processed, and where it's stored, ensuring that you have a clear understanding of data flow within your organization.
- Privacy Policy & Terms Update: We can help revise or draft GDPR-compliant privacy policies and terms of service, ensuring transparency about data practices.
- Data Protection Impact Assessment (DPIA): If required, Codedesign can assist in carrying out DPIAs to assess and mitigate risks associated with data processing activities.
- Data Breach Protocols: We can establish robust data breach notification and response protocols, ensuring that in the unlikely event of a data breach, your company responds in a timely and GDPR-compliant manner.
- Employee Training: Codedesign can provide GDPR training sessions to your staff, ensuring that everyone is aware of their responsibilities when it comes to data protection.
- Integration with GDPR-Compliant Tools: We can help integrate your platforms with GDPR-compliant third-party tools, ensuring that data is handled and stored appropriately throughout its lifecycle.
- Regular Compliance Checks: GDPR compliance is an ongoing effort. Codedesign offers periodic checks and updates to ensure that your organization remains compliant as regulations evolve and your business grows.
- Dedicated Data Protection Officer (DPO) Assistance: Codedesign can assist in the appointment or act as a dedicated DPO for your organization, overseeing and ensuring data protection strategies are upheld.
By partnering with Codedesign Digital Marketing Agency, your organization can confidently navigate the complexities of GDPR, ensuring not only compliance but also building trust with your customers and stakeholders.
FAQs - Frequently Asked Questions
What are the most common threats to personal data privacy in the digital age?
In the digital age, personal data privacy faces several significant threats that can compromise individuals' security and privacy. Phishing attacks, where malicious actors deceive individuals into providing personal information, stand as a prevalent threat. Malware, including viruses and ransomware, can infiltrate devices to steal or encrypt personal data for ransom. Unsecured Wi-Fi networks offer another avenue for hackers to intercept personal information transmitted over these networks. Social engineering tactics manipulate individuals into voluntarily disclosing their data. Lastly, inadequate privacy settings on social media and other online platforms can inadvertently expose personal information to unauthorized parties. These threats underscore the critical importance of vigilance and protective measures to safeguard personal data in an increasingly digital world.
How can individuals protect their personal information from identity theft and hacking?
Individuals can protect their personal information from identity theft and hacking through several proactive measures. Utilizing strong, unique passwords for different online accounts and enabling two-factor authentication wherever possible significantly enhances security. Regularly updating software and operating systems ensures protection against known vulnerabilities. Being wary of phishing emails and not clicking on suspicious links helps avoid malicious traps. Using secure Wi-Fi networks, especially for sensitive transactions, and employing virtual private networks (VPNs) can shield data from unauthorized access. Additionally, monitoring bank statements and using credit monitoring services can help detect unauthorized activities early. Adopting these practices can fortify personal information against common cyber threats.
What role does data privacy play in maintaining trust between businesses and their customers?
Data privacy is foundational in building and maintaining trust between businesses and their customers. In an era where personal data is a key asset, how a company collects, uses, and protects customer information directly impacts customer confidence. Transparent data privacy practices, clear communication about data usage, and strict adherence to data protection regulations demonstrate a company's commitment to safeguarding customer information. This commitment, in turn, fosters customer trust, loyalty, and positive brand reputation. For instance, Codedesign, known for its adherence to high data privacy standards, has experienced enhanced customer trust and loyalty, reinforcing the critical role of data privacy in business-customer relationships.
Can you explain the differences in data privacy concerns among various demographics and regions?
Data privacy concerns vary significantly among different demographics and regions, influenced by cultural values, regulatory environments, and awareness levels. Younger generations, growing up in a digital world, may prioritize convenience over privacy, while older individuals might be more cautious about sharing personal information online. Regions with stringent data protection laws, such as Europe with its General Data Protection Regulation (GDPR), tend to have higher public awareness and expectations regarding data privacy. In contrast, areas with less comprehensive regulations may see a different approach to data privacy, with individuals potentially less aware of their rights or the risks. This variation underscores the importance of tailored privacy policies and education efforts that consider the specific concerns and expectations of different demographics and regions.
How do data breaches affect financial losses for companies and individuals?
Data breaches can have substantial financial implications for both companies and individuals. For companies, the costs include immediate expenses related to breach investigation, legal fees, and customer notification. Additionally, there are longer-term costs like loss of business due to decreased consumer trust, reputational damage, and potential regulatory fines. For instance, businesses, including Codedesign's clients, prioritize robust data protection strategies to mitigate these risks. Individuals affected by data breaches may face identity theft, leading to unauthorized transactions, legal costs to restore their financial standing, and potential loss of employment opportunities. These financial losses highlight the critical importance of preventive measures and swift response strategies to minimize the impact of data breaches.
What measures can organizations take to prevent unauthorized data access?
Organizations can implement several measures to prevent unauthorized data access and enhance their cybersecurity posture. Establishing strong access control policies, such as role-based access, ensures that employees can only access data necessary for their roles. Regularly updating and patching software and systems protect against known vulnerabilities. Employing encryption for data at rest and in transit safeguards information from interception. Conducting regular security audits and vulnerability assessments helps identify and mitigate potential security gaps. Additionally, employee education on cybersecurity best practices is crucial for preventing data leaks caused by human error. For example, companies like Codedesign invest in comprehensive security training for their teams to fortify their defenses against unauthorized data access.
Why is it important for businesses to educate their employees about data privacy?
Educating employees about data privacy is crucial for businesses because employees play a significant role in safeguarding or inadvertently compromising data. Awareness and understanding of data privacy principles and practices empower employees to recognize and prevent potential breaches. This education helps prevent common pitfalls such as phishing attacks, improper data sharing, and unauthorized access. Furthermore, knowledgeable employees can contribute to a culture of privacy that values and protects customer data, enhancing trust and compliance with data protection regulations. Codedesign, for instance, emphasizes regular data privacy training, recognizing that informed employees are critical to maintaining high standards of data privacy and security.
How can secure data storage practices mitigate the risk of data breaches?
Secure data storage practices are fundamental in mitigating the risk of data breaches. Encrypting data at rest and in transit protects it from unauthorized access, even if security perimeters are breached. Implementing strong access controls and authentication mechanisms ensures that only authorized personnel can access sensitive data. Regularly backing up data and storing it securely can prevent loss and facilitate recovery in the event of a breach. Additionally, adopting a data minimization approach—storing only what is necessary for business operations—limits the potential damage of a breach. Companies like Codedesign that adopt these secure storage practices significantly reduce their vulnerability to data breaches and the associated risks.
What are the major differences between GDPR and CCPA, and how do they impact businesses?
The General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) are landmark privacy regulations, but they have notable differences affecting businesses. GDPR, applicable across the European Union, emphasizes the protection of personal data and the rights of individuals to control their data, requiring businesses to obtain explicit consent for data processing. CCPA, while also focusing on consumer privacy, provides California residents with the right to know about and opt out of the sale of their personal data. GDPR imposes stricter penalties for non-compliance and has a broader scope in terms of applicability to businesses outside the EU processing EU residents' data. Businesses must understand these regulations' nuances to ensure compliance, which can involve significant adjustments to their data handling and privacy policies. For global companies like Codedesign's clients, navigating these differences is crucial to operate legally and maintain customer trust.
How can companies ensure ongoing compliance with data privacy laws and regulations?
Ensuring ongoing compliance with data privacy laws and regulations requires a proactive and structured approach. This includes regularly updating privacy policies to reflect changes in laws and business practices. Conducting periodic data audits helps identify and address compliance gaps. Employee training on the latest data privacy standards and practices is crucial for maintaining an informed workforce. Implementing privacy by design, which integrates data protection into the development of business processes and systems, ensures compliance from the outset. Additionally, appointing a data protection officer (DPO) can provide dedicated oversight of data privacy practices and compliance. For businesses like Codedesign and its clients, these steps are essential in navigating the complex landscape of data privacy regulations while building trust with customers.

About Bruno GavinoBruno Gavino is the CEO and partner of Codedesign, a digital marketing agency with a strong international presence. Based in Lisbon, Portugal, with offices in Boston, Singapore, and Manchester (UK) Codedesign has been recognized as one of the top interactive agencies and eCommerce agencies. Awarded Top B2B Company in Europe and Top B2C company in retail, Codedesign aims to foster personal relationships with clients and create a positive work environment for its team. He emphasizes the need for digital agencies to focus on data optimization and performance to meet the increasingly results-driven demands of clients. His experience in digital marketing, combined with a unique background that includes engineering and data, contributes to his effective and multifaceted leadership style. |

About CodedesignCodedesign is a digital marketing agency with a strong multicultural and international presence, offering expert services in digital marketing. Our digital agency in Lisbon, Boston, and Manchester enables us to provide market-ready strategies that suit a wide range of clients across the globe (both B2B and B2C). We specialize in creating impactful online experiences, focusing on making your digital presence strong and efficient. Our approach is straightforward and effective, ensuring that every client receives a personalized service that truly meets their needs. Our digital agency is committed to using the latest data and technology to help your business stand out. Whether you're looking to increase your online visibility, connect better with your audience, get more leads, or grow your online sales. For more information, read our Digital Strategy Blog or to start your journey with us, please feel free to contact us. |
CodeDesign is leading:
- Digital Agency
- Digital Marketing Agency
- Digital Ecommerce Agency
- Amazon Marketing Agency

Add comment ×